In this article we delve into the topic of security within the crypto airdrop world.
Oftentimes when doing airdrop hunting, in other words: searching for protocols and infrastructure that could distribute tokens to your community, there is a risk of running into scams or interacting with malicious smart contracts.
Let’s see together how to protect oneself from these risks and increase one’s security.
The issue of security in crypto airdrops
Cryptocurrency airdrops are a great way to increase liquidity in investments, but at the same time they underlie cybersecurity risks that one must be very careful about.
Generally speaking, the individuals who are most successful in this particular world are the same ones who are very active within crypto communities and conduct a large number of on-chain transactions, coming into contact with as many smart contracts.
The main risk in all of this, is that such massive exposure could result in the loss of all the funds held in the wallet in which one is operating, especially if one does not have a thorough 360-degree knowledge of cybersecurity issues.
In particular, all it takes is a single mistake, where users approve a scam contract or come into contact with bogus txs, to cause serious damage to their finances.
On some occasions, even in the face of all the necessary precautions before starting airdrop hunting, there is still a risk of being hit by hacks and exploits in cases where it is the software you are working on that is being attacked.
The latter risk should be considered in any activity belonging to the crypto sector, but more importantly, it should be taken into account even more when conducting a transaction volume of, say, 20 to 30 transactions per day.
For instance, think of the recent case of Atomic Wallet software tampering, in which a portion of the wallet’s users lost a total of $100 million.
Surely among these, there must have been a portion of individuals using the non-custodial wallet to interact with DeFi projects with a view to obtaining an airdrop.
The intention in this article is not to scare and spread terror about a conceptually “random” activity, but rather to highlight the risks one must necessarily run into in order to best manage the risk.
Indeed, it is not the risk itself that is a problem, but the high exposure to which many people subject themselves, without protective measures.
In the next section we will look at how to defend against these risks and increase one’s degree of security in the fantastic universe of cryptocurrency airdrops.
How to increase one’s security when airdrop hunting
To increase one’s security, first and foremost, one should create a special wallet to be used exclusively when airdrop hunting.
It is absolutely inadvisable to manage one’s personal crypto holdings with funds intended for daily interaction with Web3 protocols.
One’s primary holdings should be kept in a hardware wallet, to be used as little as possible, only for strictly necessary transactions, such as cashing out or changing one’s asset allocation.
By following this first rule, you will surely have eliminated the risk of losing everything!
Secondly, there is a whole series of precautions to consider in order to secure one’s cryptocurrency wallet from malicious parties.
The most experienced in the Web3 world know very well by now the fact that hardware wallets turn out to be much more secure than software wallets, due to a number of reasons that we will not explain here.
Favor wallets such as Ledger, Trezor, Jade, Bitbox and Coldcard over software versions such as MetaMask, and Trustwallet.
Generally, the hardware wallets just mentioned allow connecting to the MetaMask interface while inheriting all the conveniences of the latter, maintaining the security of offline private key storage.
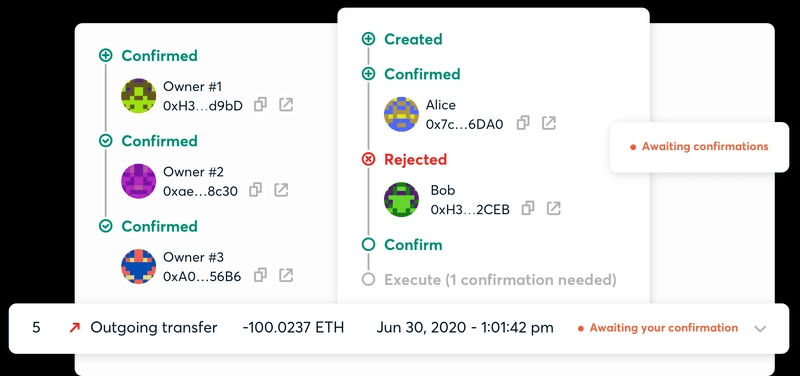
If you are operating an airdrop hunting activity in a group, NEVER use a software wallet and store private keys with multiple people because doing so multiplies the risks of hacking.
It is much better to take advantage of multi-signature wallets such as Safe, which are also used by DAOs and whales managing multimillion-dollar figures.
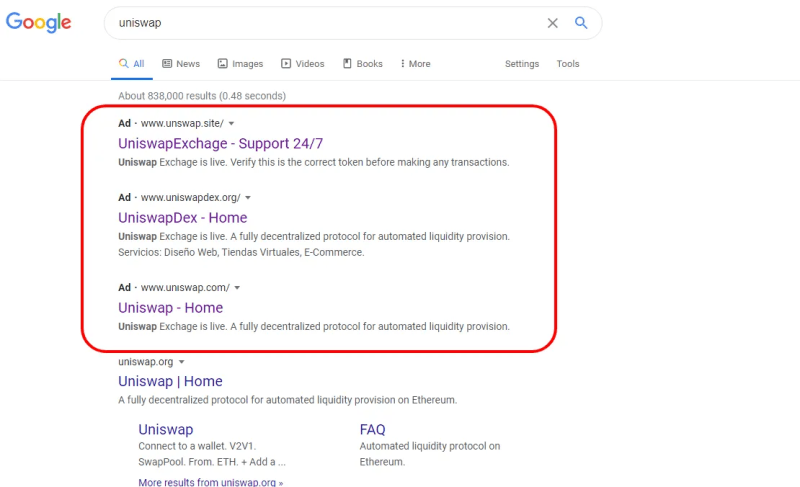
Another tip to offer to improve the security aspect is to always check the sources of the websites you are about to come into contact with.
Even if you are a seasoned user and have used the decentralized platforms of the DeFi world many times, it is always a good idea to avoid typing the name of the dApp into search engines and go by trusted sources such as the OFFICIAL Twitter pages, “CoinMarketCap,” “DefilLama,” “DappRadar,” or simply the ecosystem pages (in case you are operating for a chain airdrop such as zkSync, Starknet, PolygonZKEvm, etc.).
Finally, the last but not least tip, if you are new to Twitter, beware of fake profiles talking about airdrop and token claims.
Unfortunately, there are an avalanche of scam profiles circulating that recreate purpose-made web interfaces to look similar to the originals, the only difference being that they hide malicious smart contracts that will clean out your wallet.
Always double-check to make sure there really is a supposed airdrop coming. Rest assured that when it happens the whole world will be talking about it, so you will have no trouble noticing it.
2 very useful tools to protect yourself
In an effort to increase safety from the systemic risk of airdrop hunting activity, we point out 2 very useful tools to protect yourself.
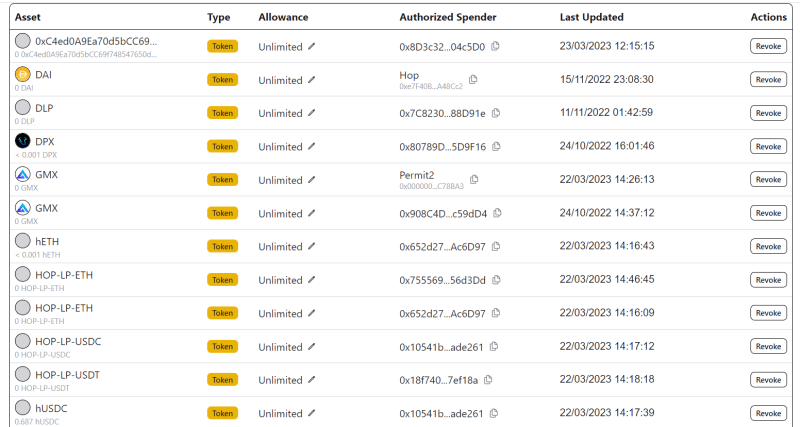
The first is called “Revoke cash” and allows you to revoke certain types of authorization you have granted in the past to decentralized platforms.
Generally before executing a smart contract transaction, you are asked to approve the contract often.
Although this is mandatory and not necessarily dangerous at first, it might be the case that the platform you have been operating on and the smart contract are being tampered with, potentially resulting in the risk of contamination of your wallet.
To be on the safe side, after you have interacted with unfamiliar dApps in the crypto world, go to the official Revoke cash website, enter your address in the search bar and click on “revoke” based on the authorization you want to remove.
The tool also includes a section called “exploits” where you can check in real time which protocols and blockchains have been compromised.
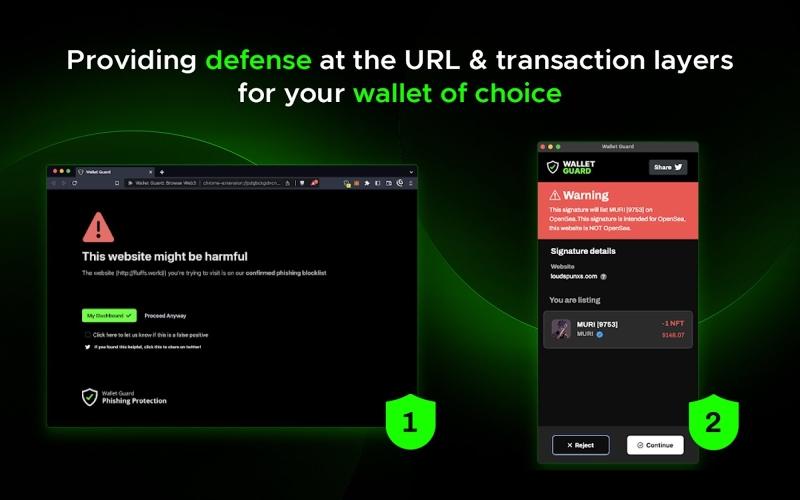
The second tool, which is very convenient for security issues, is “wallet guard.”
It is a free extension that allows you to check the details of the transactions being signed when coming into contact with a smart contract.
Without this tool, in order to decipher what clauses are imposed by the various contracts we are about to sign would have to go and read the source code (granted that we have the knowledge to distinguish legitimate and non-legitimate cases).
Wallet guard makes our lives easier and provides us with alerts on phishing sites, highlighting potential dangers we are running into.
An extra shield of protection that is extremely necessary for those who continuously practice the profession of airdrop hunter.
Always remember: safety comes first!